Burp Suite Pro real-life tips & tricks: Authentication engine for command-line tools
Below is a nice Burp trickery I’ve learnt from Ryan and extended it also for apps that are using token-based session handling.
To put long story short: it often convenient to set up a session using browser (on top of the Burp) and then reuse it in various command line tools. Below is exactly that case for two scenarios: cookie-based session handling and token-based session handling.
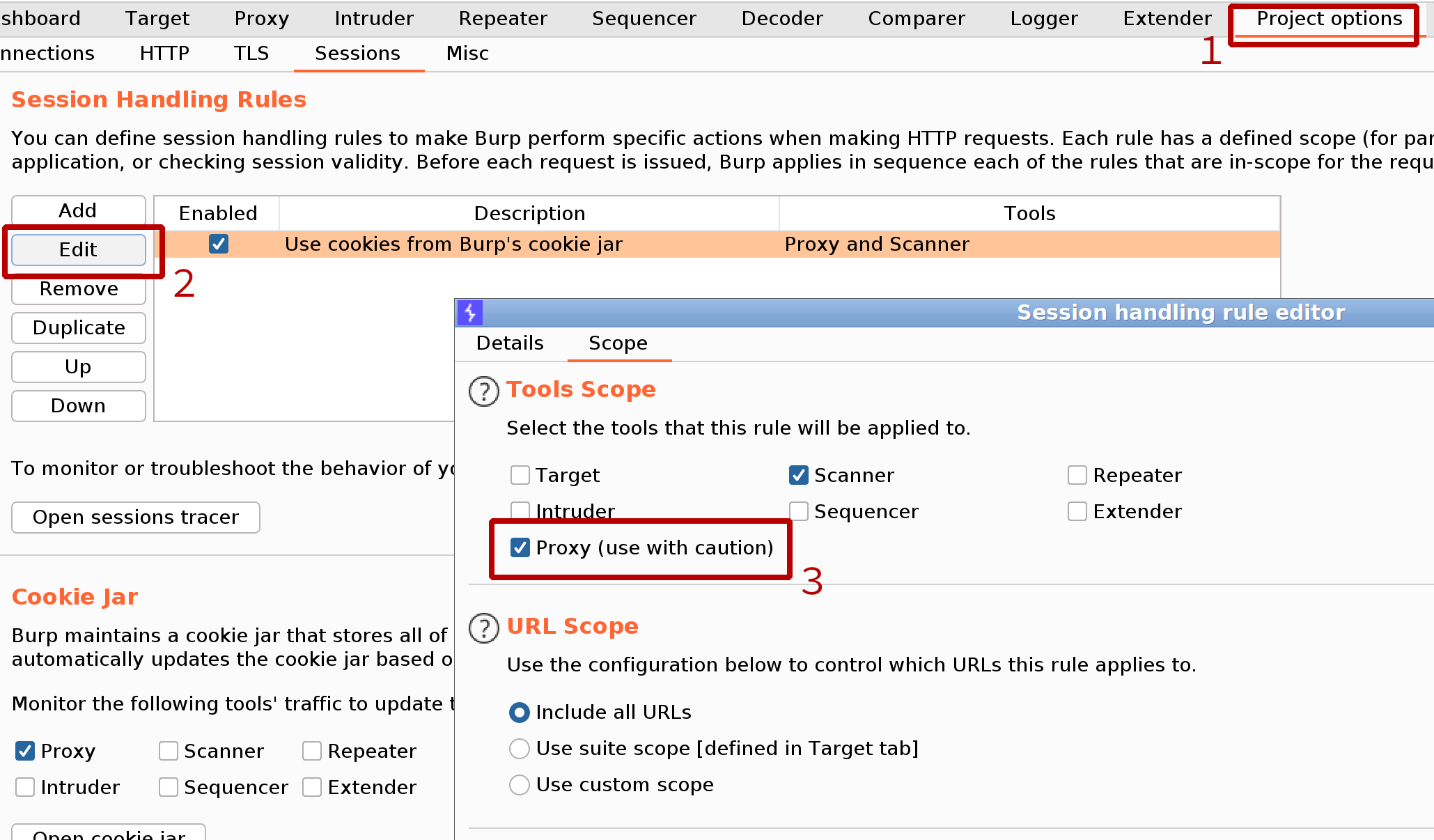
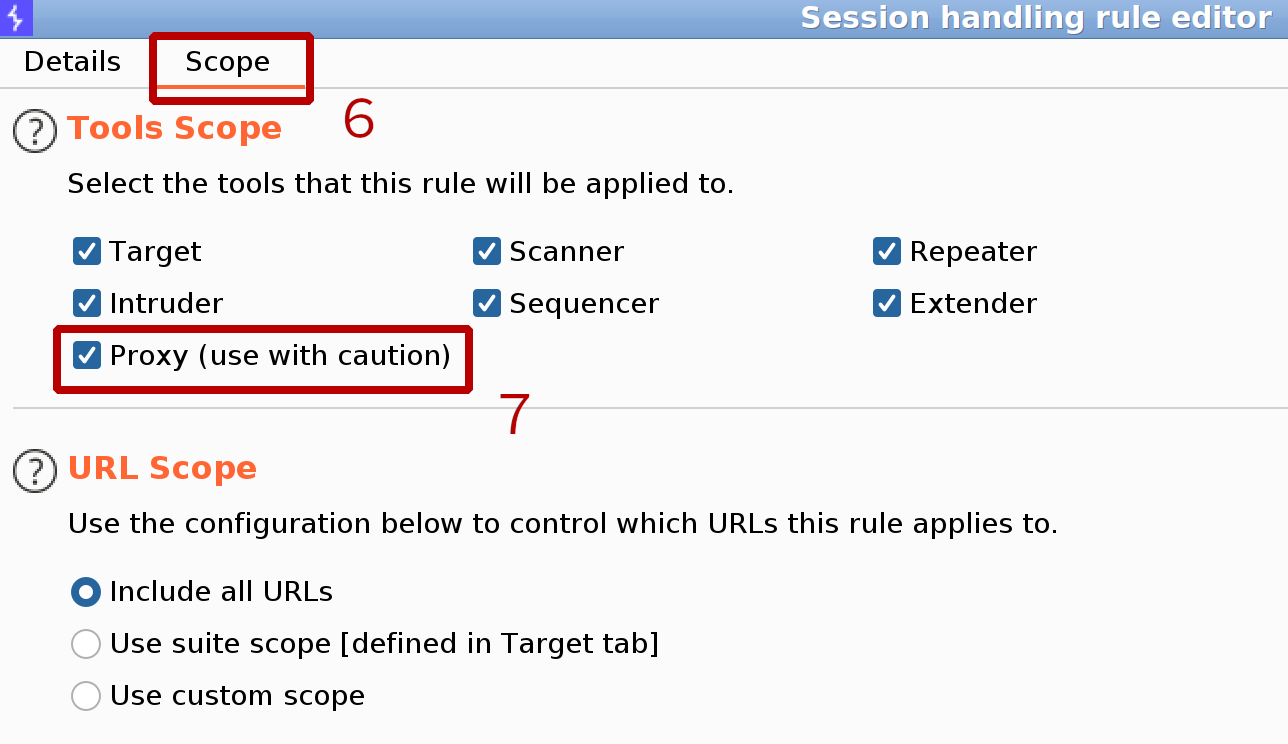
In case of cookie-based session handling we just need to add Proxy to Tools Scope, as shown below:
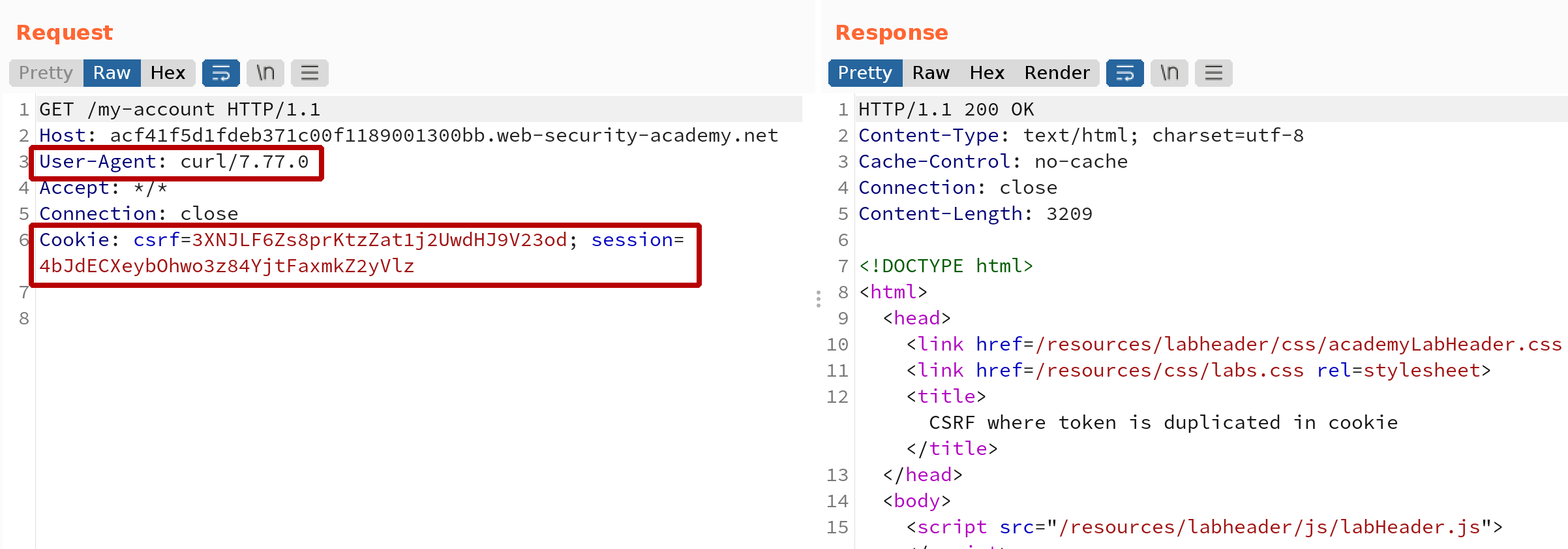
To verify the setting we instruct curl to use Burp as a proxy:
$ curl -k -x 127.0.0.1:8081 -s https://acf41f5d1fdeb371c00f1189001300bb.web-security-academy.net/my-account
In Burp Logger we can observe that session handling rule was properly applied and added required cookies:
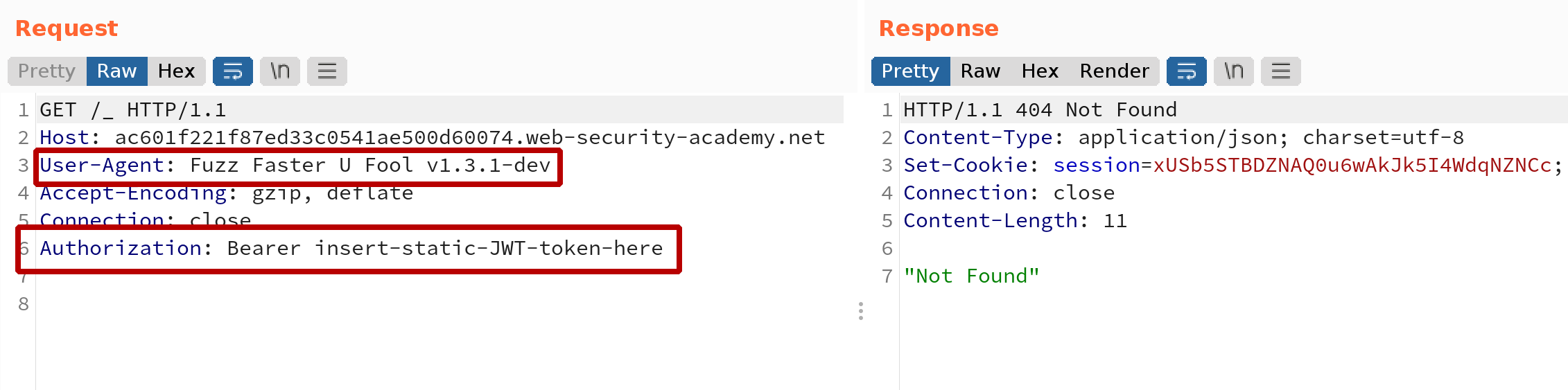
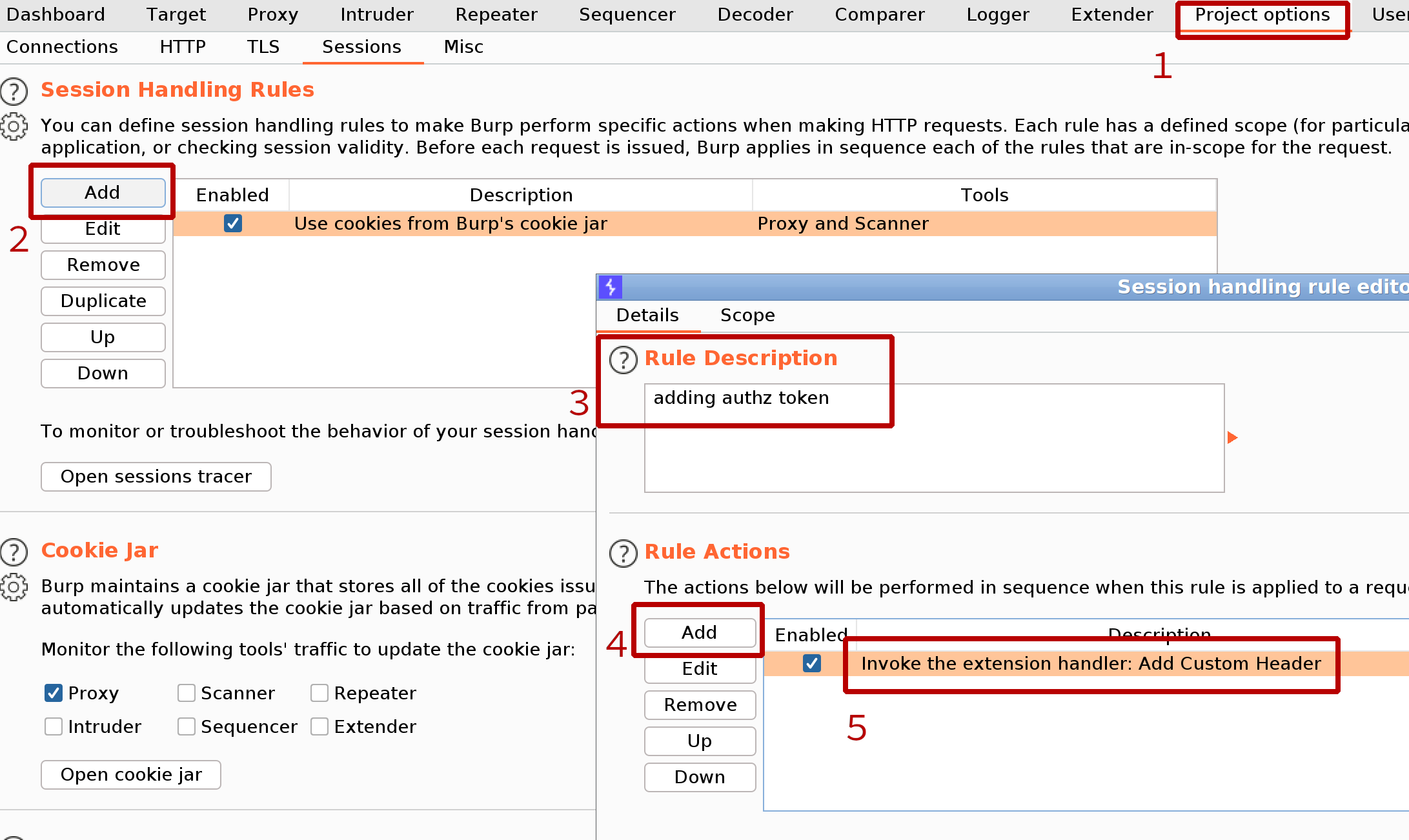
In case of applications that use token-based session handling we will use Add Custom Header extension to add token and then instruct a session handling mechanism to invoke extension’s handler as an action:
Adding Proxy to Tools Scope:
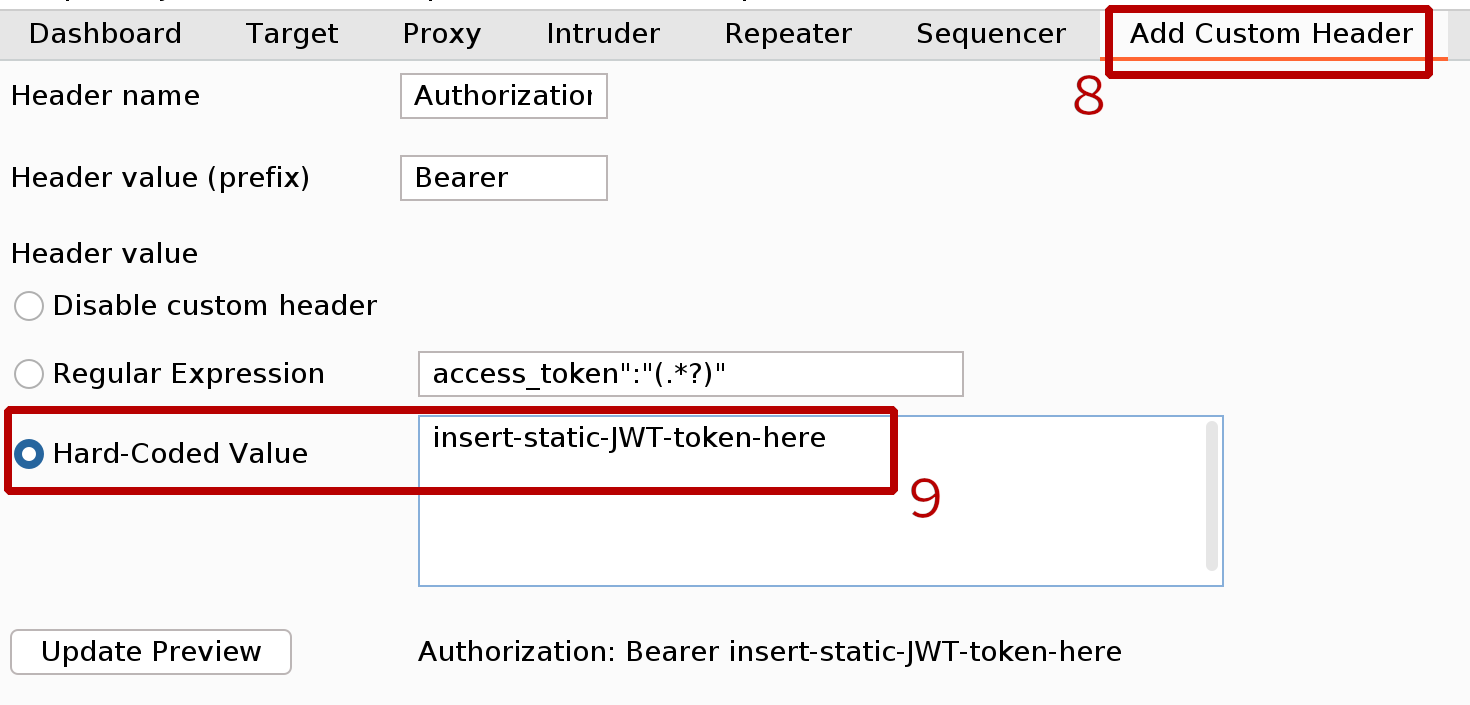
Configuring Add Custom Header extension to use hard-coded token:
This time we will use ffuf command line tool to verify if session handling rule was applied, as shown below:
$ ffuf -x http://127.0.0.1:8081 -u https://ac601f221f87ed33c0541ae500d60074.web-security-academy.net/FUZZ -w ~/bad_chars.txt
In Burp Logger we can observe that session handling rule was properly applied and added the token: