Mobile apps penetration testing 2020
There are already great resources about mobile app security testing out there. So here I’m mostly just keep track of resources/approaches that worked for me (with additional comments), to have it in one place for the sake of future reference.
Reference
The Mobile Application Security Verification Standard (MASVS) - defines high-level requirements for robust and secure application. So that’s the great place to start for the pen tester to start verifying whether those reqs are met by the tested application.
The Mobile Security Testing Guide (MSTG) - while the MASVS defines what to look for during the mobile pen test, the MSTG discusses the tools and techniques that could be used for the testing.
I found MSTG little hard to navigate, so here are the direct links for chosen MASVS requriements mapped into MSTG sections (currently only for Android devices):
V2: Data Storage and Privacy Requirements
Testing Local Storage for Sensitive Data: MSTG-STORAGE-1 and MSTG-STORAGE-2
Testing Local Storage for Input Validation: MSTG-PLATFORM-2
Testing Logs for Sensitive Data: MSTG-STORAGE-3
Determining Whether Sensitive Data is Sent to Third Parties: MSTG-STORAGE-4
Determining Whether Sensitive Stored Data Has Been Exposed via IPC Mechanisms: MSTG-STORAGE-6
Checking for Sensitive Data Disclosure Through the User Interface: MSTG-STORAGE-7
Testing Backups for Sensitive Data: MSTG-STORAGE-8
Finding Sensitive Information in Auto-Generated Screenshots: MSTG-STORAGE-9
Checking Memory for Sensitive Data: MSTG-STORAGE-10
Testing the Device-Access-Security Policy: MSTG-STORAGE-11
V4: Authentication and Session Management Requirements
Mobile Authentication and Session Management testing: Overview
Verify presence of authentication mechanism: MSTG-AUTH-1
V5: Network Communication Requirements
Verifying Data Encryption on the Network: MSTG-NETWORK-1 and MSTG-NETWORK-2
Testing Endpoint Identify Verification: MSTG-NETWORK-3
Testing Custom Certificate Stores and Certificate Pinning: MSTG-NETWORK-4
V6: Platform Interaction Requirements
Verify that an application requests the minimum set of permissions necessary: MSTG-PLATFORM-1
Verify validation of external input:
MSTG-PLATFORM-2: injection flaws MSTG-PLATFORM-2: fragment injection
Misc
Some other misc references that I found handy:
OWASP Mobile Top 10 - most common security issues present in mobile apps.
Basic (mobile) Security Testing - intro to mobile app pen testing
Andoid emulator-commandline - Andoroid emulator command line reference
Environment preparation
Tooling
Tools used:
Android Studio (available at AUR: https://aur.archlinux.org/packages/android-studio/)
android-apktool (available in BlackArch)
drozer (avilable in BlackArch)
uglifyjs2
Launching Android Emulator
One-time steps in Android Studio
- Create new project choosing ‘Profile or debug APK’ and check what API version it uses:
grep 'platformBuildVersionCode' ~/ApkProjects/<APK_FILENAME>/AndroidManifest.xml
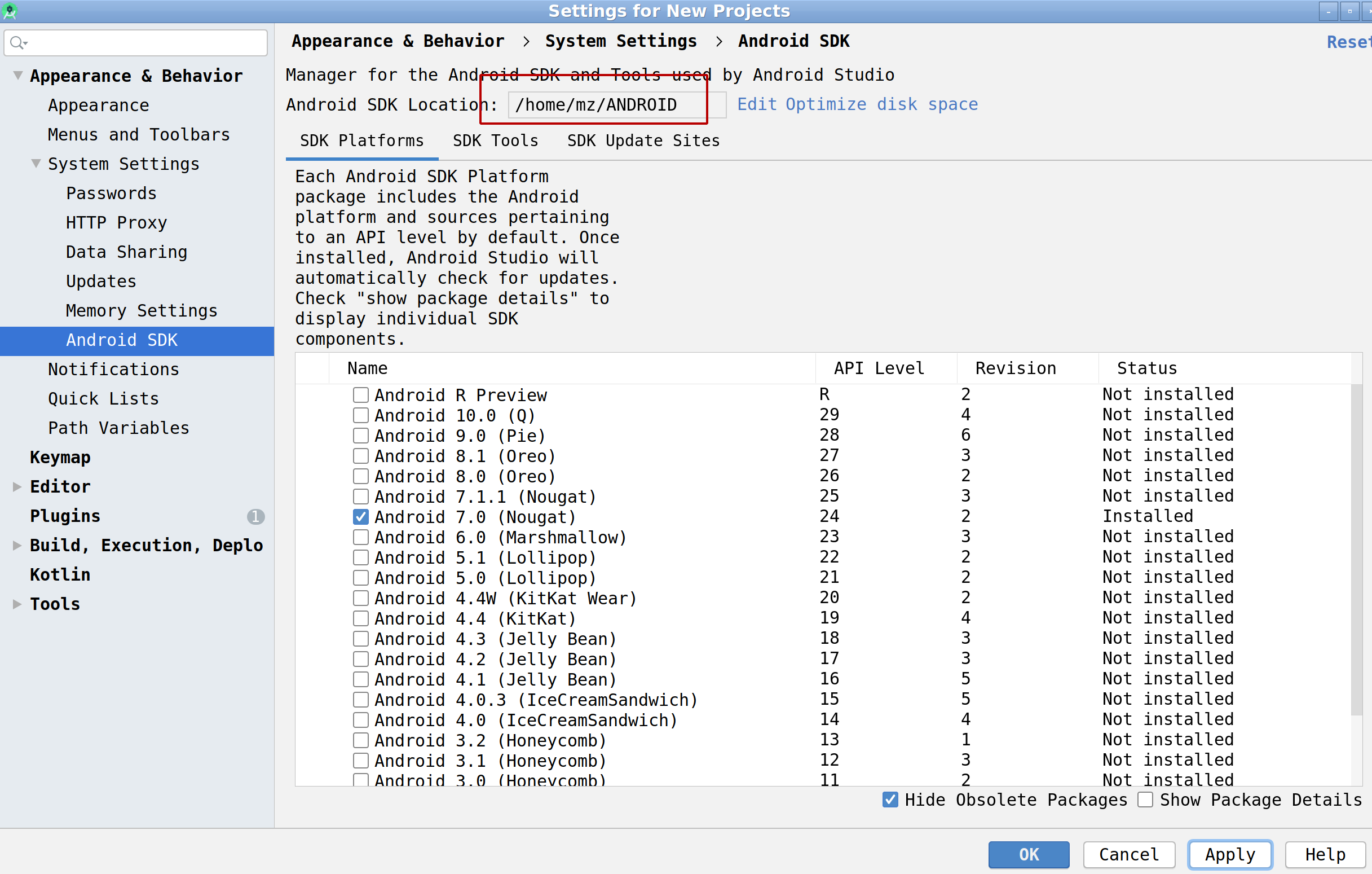
- Install SDK version required by tested application:
Tools -> SDK Manager -> Android SDK
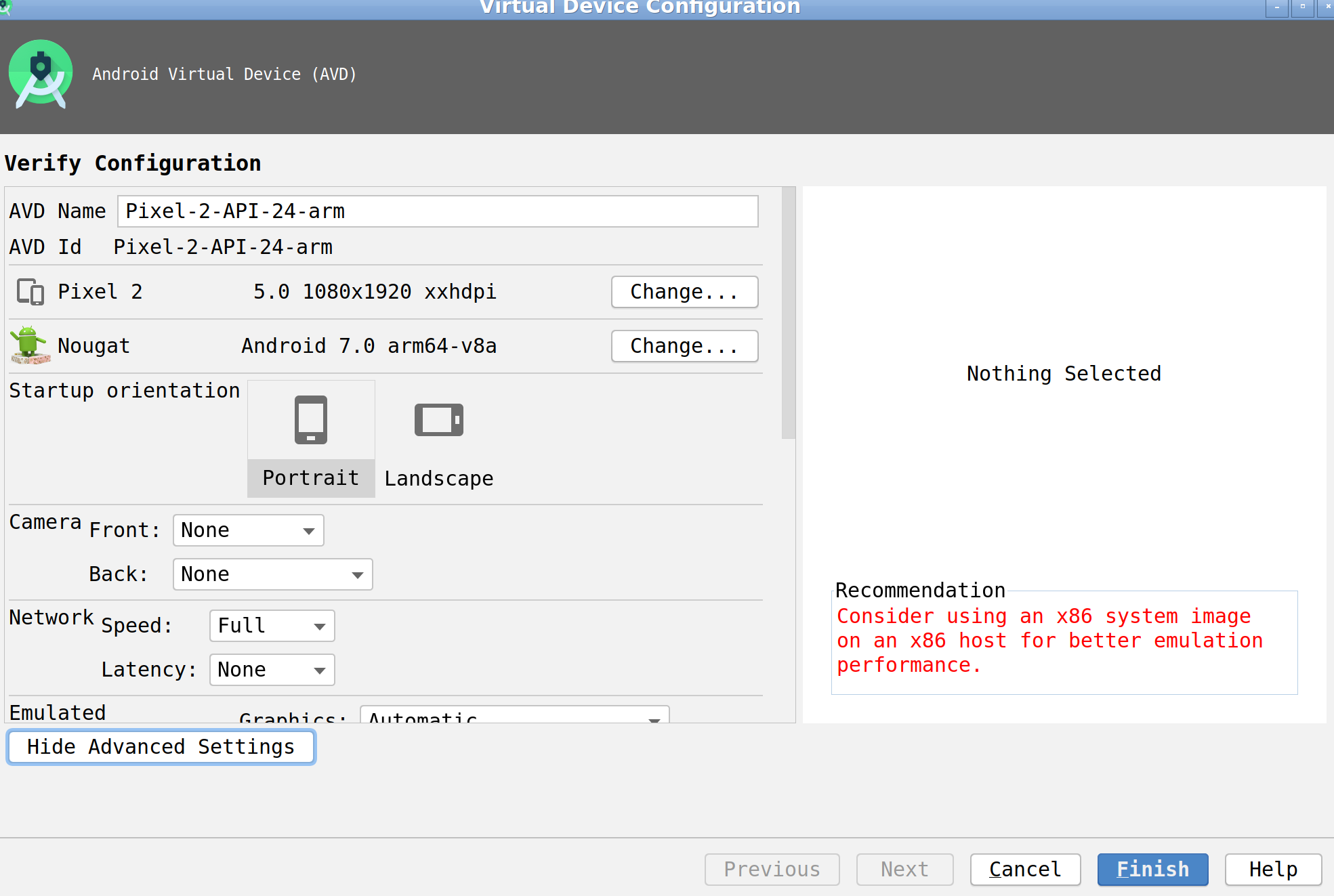
- Create device image (AVD)
Tools -> AVD Manager -> Create Virtual Device ...
- Make sure that you choose Google APIs system image as only this will allow you to install not signed applications.
- If possible prefer working with x86/x86_64 images vs arm-based images as the former one are (obviously) much faster.
After completion:
- your virtual device (avd) is located here:
~/.android/avd/, - Android SDKs are here:
~/ANDROID/platforms/(provided that~/ANDROIDdirecotry was chosen as SDK location), - system image lands here:
~/ANDROID/system-images/, - and your Android Studio projest will be here:
~/ApkProjects/.
Once done any subsequent device run can be done via command line:
~/ANDROID/emulator/emulator -list-avds
~/ANDROID/emulator/emulator -writable-system -avd <YOUR_AVD_NAME> -http-proxy 127.0.0.1:8088 -dns-server 1.1.1.1 -no-snapshot
Deploying target APK and other stuff onto the device
Decompilation and busic static analysis with qark:
Installation:
virtualenv --python=python3 ~/virtual-python3
source ~/virtual-python3/bin/activate
pip install qark
qark --build-path apk.decompiled --report-type json --apk <APK_FILENAME>
Install drozer agent:
adb -s emulator-5554 install /usr/share/drozer/drozer/lib/standard-agent.apk
adb -s emulator-5554 forward tcp:31415 tcp:31415
<launch drozer's Embedded Server on the device via GUI>
drozer console connect
For drozer usage scenarios see here.
Instrument APK with objection:
Install:
source ~/virtual-python3/bin/activate
pip3 install -U objection
Patch APK:
objection patchapk --source <APK_FILENAME>
Install target (patched) APK:
adb devices
adb -s emulator-5554 install <APK_FILENAME>
NOTE: installed patched application will be paused. Run objection explore on the host to resume it.
Installing TLS cert on Android
I’ve stumbled upon following issue while trying to install my TLS certificate on Andorid device:
- It seems that Android Q (10) does not allow to mount root partition in R/W mode anymore which prevents from adding certificate to system trust store.
Haven’t found solution to it so I’m currently using Android 9.
Here’s the mitmproxy’s way to add the cert to the trust store, to work with Burp Suite certificate, following steps should be followed:
Export Burp CA certificate, go to:
Proxy -> Options -> Import/Export CA certificate -> Export certificate in DER format
Renaming CA certificate (required to be accepted by the Android device):
openssl x509 -inform DER -subject_hash_old -in burp-cert.der | head -1
mv burp-cert.der <output-from-above>.0
Installing the certifiate to trust store:
adb root
adb shell "mount -o rw,remount /"
adb push <output-from-above>.0 /system/etc/security/cacerts
adb shell "chmod 664 /system/etc/security/cacerts/<output-from-above>.0"
# Reboot the device:
adb reboot
# For troubleshooting:
Make sure that after rebooting your certificate is present at:
Settings -> Trust Certificates
Ideas / approaches / tooling to try
https://github.com/nccgroup/house
Iphone emulation on Linux:
https://askubuntu.com/questions/539233/how-to-install-an-iphone-application-in-linux
https://github.com/ios-control/ios-deploy